EON INSIGHTS
Cryptography Discovery Platform
Built for security leaders who can’t afford cryptographic blind spots
CRYPTOGRAPHIC SECURITY POSTURE VISIBILITY
Most organizations can’t answer a simple question: “What cryptographic algorithms are actually running in our infrastructure?”
If you’re deploying encryption without visibility, you’re essentially hoping your security posture is sound. With quantum computing on the horizon and regulators demanding proof of cryptographic controls, that’s no longer acceptable.
🔍 Complete Cryptographic Inventory
Every TLS connection, SSH key, certificate, and cipher suite across your entire infrastructure—automatically discovered without code changes or operational disruption.
⚠️ Vulnerabilities That Matter
Weak algorithms, deprecated protocols, and misconfigured endpoints flagged and prioritized by business impact. No alert fatigue. Just actionable risks.
✅ Compliance Evidence
One-click reports proving you meet PCI-DSS, NIST 800-52, GDPR, HIPAA, and NIS2 requirements. Built for auditors and regulators, not internal IT processes.
MULTIPLE PROTOCOLS
TLS, SSH, IPSEC, OPENVPN . . .
REALTIME MONITORING
Continuous Realtime Detection
ZERO INTERRUPT
Out of band, passive & active monitoring
The Challenge
Most organizations have no idea what cryptographic algorithms are running in their infrastructure. With quantum computing on the horizon, this blind spot is a ticking time bomb.
Hidden Vulnerabilities
Legacy TLS versions and weak cipher suites lurking in your network create attack vectors you can’t see.
Compliance Gaps
PCI-DSS, NIST, and GDPR require cryptographic controls you can’t prove without visibility.
Quantum Threat
Post-quantum cryptography transition requires knowing exactly what needs to be upgraded.
Capabilities
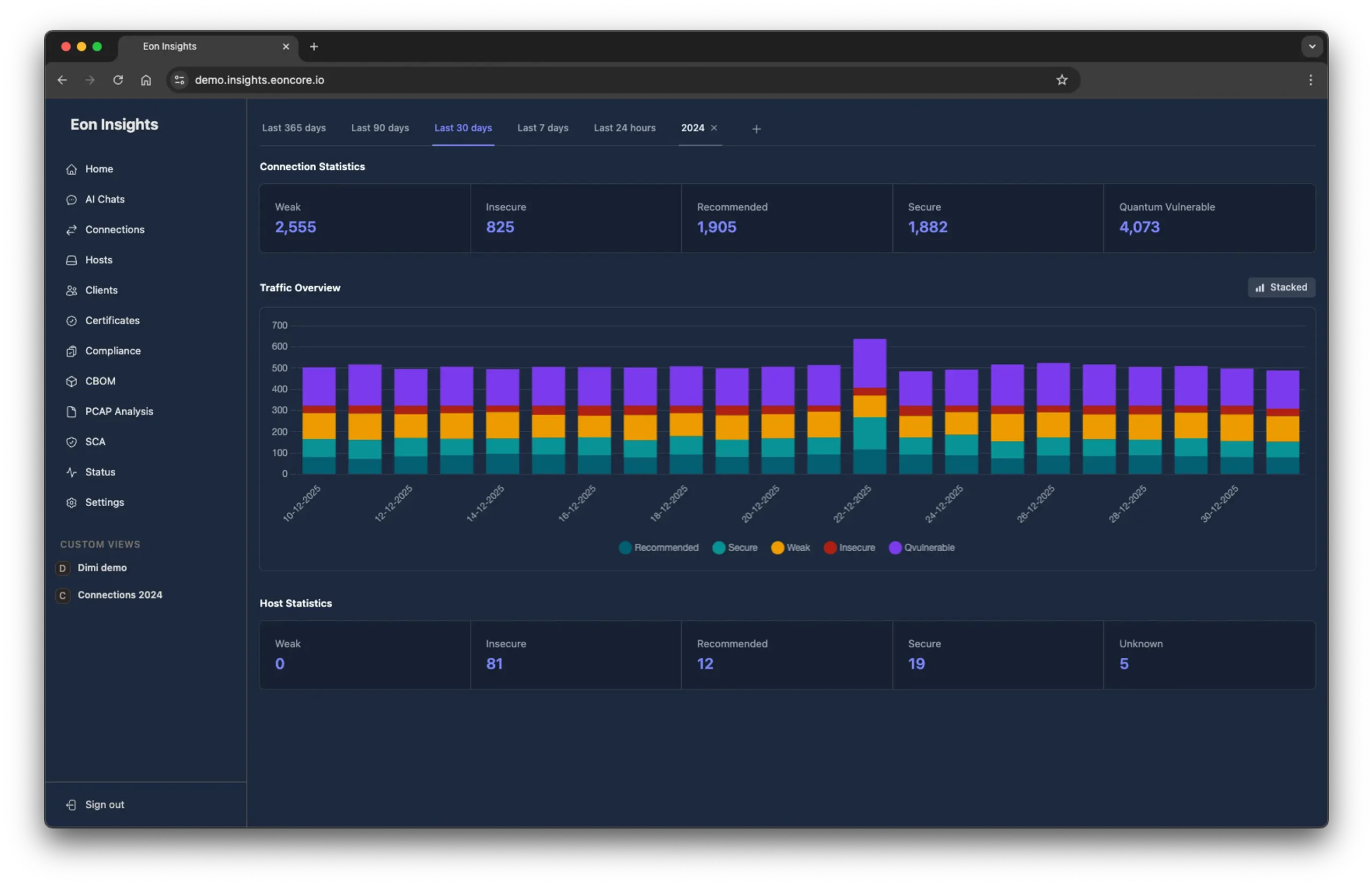
Complete Cryptographic Visibility
From passive traffic analysis to active scanning, Eoncore Insights gives you full control over your cryptographic security posture.
Real-Time Traffic Analysis
Stop guessing what's connecting to what. All without slowing down your network or disrupting production systems. You catch legacy clients, abandoned systems, and misconfigurations before they become breaches. Your security team goes from "we hope we're compliant" to "we know we're compliant." Passively monitor every encrypted connection crossing your network.
- See every client and server communicating securely
- Discover which cipher suites are in use (and which are weak)
- Understand certificate chain integrity and expiration risks
- Learn unauthorized or suspicious connection patterns
Vulnerability Detection
Stop waiting for pen tests to find your weak spots.Eon Insights continuously scans your infrastructure and surfaces vulnerabilities.
- Weak ciphers and deprecated TLS versions still in use
- Certificates expiring in the next 90 days
- Cryptographic debt accumulating in legacy systems
- Configuration mismatches between policy and reality
Security Analytics
Comprehensive dashboards showing cipher suite distribution, TLS version adoption, and security trends over time.
Compliance Automation
Go from months of manual audit prep to one-click proof. Eon Insights generates audit-ready reports that map your actual infrastructure against regulatory requirements.
AI-Powered Insights
Stop digging through dashboards. Ask natural language questions and get instant answers. Build your own reports. Create custom views. Make data accessible to your whole team.
- "Which systems are still using TLS 1.0?"
- "Show me all connections with cipher suites weaker than 256-bit"
- "Which certificates expire in the next 60 days?"
How It Works
From Discovery to Remediation
A systematic approach to cryptographic security management
01
Discover
Deploy lightweight network sensors to passively capture TLS traffic. Within hours, you’ll have a complete inventory of every cryptographic connection in your environment.
- Zero-impact passive monitoring
- Automatic asset discovery
- Certificate inventory
02
Analyze
Our analytics engine categorizes every connection by security level, identifies vulnerabilities, and maps your cryptographic attack surface.
- Cipher suite classification
- Risk scoring and prioritization
- Trend analysis and anomaly detection
03
Remediate
Get actionable recommendations and track remediation progress. Export reports for stakeholders and auditors with full evidence trails.
- Prioritized remediation guidance
- Progress tracking dashboards
- Audit-ready documentation
Compliance
Meet Regulatory Requirements
Automated compliance checking against industry standards and regulatory frameworks
PCI-DSS
Payment Card Industry
Requirement 4: Encrypt transmission of cardholder data across open networks with strong cryptography.
NIST
NIST SP 800-52
Guidelines for the selection, configuration, and use of TLS implementations.
GDPR
Data Protection
Article 32: Implement appropriate technical measures including encryption of personal data.
HIPAA
Healthcare
Technical safeguards for protecting electronic protected health information in transit.
NIS2
EU Critical Infrastructure
EU directive requiring essential sectors including healthcare to implement strong cryptographic controls.
Industries
Built for Enterprise Security Teams
Financial
Legacy trading systems still using TLS 1.1. Your last pen test was 6 months ago. Auditors will ask “what changed since then?” and you won’t have an answer.
Real-time monitoring catches TLS downgrades and cipher weaknesses immediately. One-click PCI-DSS evidence. Auditors see a live snapshot of your cryptographic controls, not a stale report.
Healthcare
HIPAA enforcement is increasing. You know patient data is encrypted, but can you prove *which* algorithms are protecting it? Can you prove certificates aren’t expiring mid-transmission?
Complete cryptographic inventory across all clinical systems. Automated HIPAA compliance reports. Your compliance team can prove every byte of patient data is protected with appropriate cryptography—to regulators, to patients, to your board.
Technology
Microservices, containers, and APIs multiply daily. Each adds new encrypted connections. You can’t deploy sensors everywhere. Legacy security tools don’t understand modern APIs or container cert rotation.
Passive, agent-less monitoring across Kubernetes, serverless, and hybrid environments. See every API connection. Detect misconfigured certs before they break production. Your infrastructure team goes from “we hope APIs are secure” to “we know they are.”
Government
Post-quantum cryptography mandates are coming. NIST will standardize PQC in 2024. You need to know which systems will need to transition—now.
Comprehensive inventory of every cryptographic algorithm in use. Clear roadmap showing what needs to be replaced. Automated preparation for migration to quantum-resistant protocols. Your team moves from “we’re not ready” to “we have a plan.”
AI & LLM
AI agents and LLMs make external API calls continuously. Each call is a potential cryptographic weakness. TLS misconfigurations, cert issues, and algorithm downgrades compound as call volume scales.
Monitor all LLM-to-API communications for weak cryptography. Catch certificate expirations before they break your models. Ensure API keys and model outputs are protected with strong encryption. Your ML ops team gets visibility into the security layer they’ve been ignoring.
Ready to See What’s Running in Your Network?
Get a personalized demo and discover your cryptographic blind spots.
